I am working with a customer where we want to enable multi-factor authentication for their users as a measure to secure their environment. But when you enable MFA and a user logs on for the first time, the user has to enter his mobile phone number, even if the mobile phone number is populated in on-premises Active Directory and synchronized to Azure Active Directory (which is default).
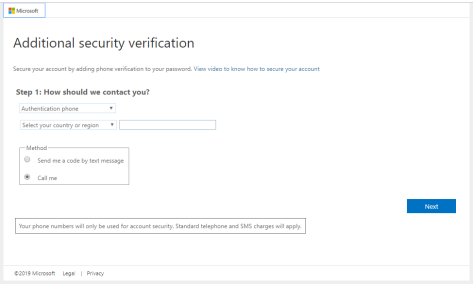
When you check the user account in the Azure AD portal, you can see that the mobile phone number is synchronized, but the authentication phone number is empty.
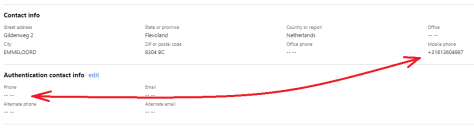
This is not a desired solution, if a user can set a new mobile phone during logon, a malicious user can do this as well. A typical user will logon shortly after the MFA is set, but especially when doing bulk changes this might not be the case. And when a user account that is MFA enabled, but hasn’t set the authentication phone property is compromised you’re screwed.
Out of the box there’s no easy way to prepopulate the authentication phone number. The authentication phone number is not store in on-premises Active Directory, it’s an Azure AD property. The property to control the strong authentication is called StrongAuthenticationMethods and you can set this using PowerShell. When you set this, the authentication phone number is still prepopulated, but when the mobile phone number is synchronized, this is used in the first place.
To set this StrongAuthenticationMethods property you can use the following PowerShell commands:
Connect MsolService $UserPrincipalName = "j.brown@exchangelabs.nl" $SMS = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationMethod $SMS.IsDefault = $true $SMS.MethodType = "OneWaySMS" $Phone = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationMethod $Phone.IsDefault = $false $Phone.MethodType = "TwoWayVoiceMobile" $PrePopulate = @($SMS, $Phone) Set-MsolUser -UserPrincipalName $UserPrincipalName -StrongAuthenticationMethods $PrePopulate
Now when the user logs on for the first time with MFA enabled, he’s presented the enter code dialog box, without having to enter a mobile number first.
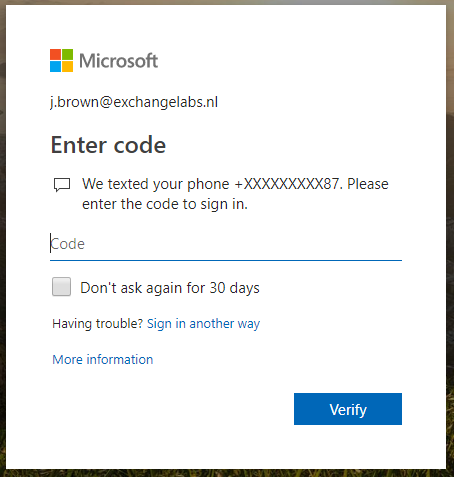
If you do this, and the mobile phone number is not set in on-premises Active Directory, MFA will still try to use the mobile phone number, but nothing will happen as shown in the following screenshot:

Since there’s no mobile phone number to use, and no option to add this anymore directly by the user you’re stuck here (until the mobile phone number is added to on-premises Active Directory of course).
Note. If you want to enable MFA using PowerShell, you can use the following commands (and maybe combine them with the commands mentioned earlier):
$Strong = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationRequirement $Strong.RelyingParty = "*" $Strong.State = "Enabled" $MFA = @($Strong) Set-MsolUser -UserPrincipalName j.smith@exchangelabs.nl -StrongAuthenticationRequirements $MFA
More information
- Pre-Provisioning Microsoft Azure Multi-Factor Authentication for Users – https://blogs.technet.microsoft.com/cloudpfe/2014/04/09/pre-provisioning-microsoft-azure-multi-factor-authentication-for-users/
- How to require two-step verification for a user – https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates
You can sync the mobile number to AAD so it is pre polulated in the mfasetup , user still has to do a manual step to register it/validate it. The Exchange option in AD Connect enabled the sync of mobile phone. See https://docs.microsoft.com/en-us/azure/active-directory/hybrid/reference-connect-sync-attributes-synchronized#exchange-online
PS. Thanks for the info yesterday 🙂
LikeLike
We have implemented the prepopulating via this method, and it’s working like a charm! Thank you!
LikeLike
I have tried above steps and now user are not getting Additional security information tab but the number we are using to get code in not populating in Authentication contact info.
And I want that number should be reflect in Authentication contact info
LikeLike
How you found a way to do this through Power Automate?
LikeLike
Jaap, thanks for the great write up. I know your focus was on AADC synced accounts. Have you tried to do this using AAD cloud-only accounts? We’ve been trying by loading the MobilePhone field but it appears to run into the same issue where you get the error message and are stuck. If the MobilePhone field is populated, from either AD or AAD, it seems like this should work properly. Is there something behind-the-scene that allows it only to work with AD synced accounts? Using the MobilePhone field we can get it to populate the MFA phone number prompt but we cannot use the -StrongAuthenticationMethods attribute – that causes the error.
LikeLike
That’s an interesting scenario, I haven’t look at that but will do the next couple of days.
LikeLike
Got same problem in my case, Im trying to solve this for almost a month. Would be glad for any help 🙂
LikeLike
I have seen this problem and looking into it (when time permits)
LikeLike
This method doesn’t work anymore for cloud-only users and will stop working for synchronised users by May 1st 2021. See: https://techcommunity.microsoft.com/t5/azure-active-directory-identity/updates-to-managing-user-authentication-methods/ba-p/1751705
The supported way to register authentication phone numbers is here: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userdevicesettings#manage-methods-using-powershell
Contact me @andrescanello on Twitter if you have questions
LikeLike
Thanks for the heads-up.
LikeLike