When you are troubleshooting an ADFS deployment, or you’re working with a 3rd party vendor on authentication issues, or maybe when you’re just interested in a deep dive in your ADFS environment, then there are multiple tools available from Microsoft for testing purposes.
To learn more about ADFS in general the Active Directory Federation Services Wiki Portal is a good starting point, for online tools the ADFS Help from Microsoft (https://adfshelp.microsoft.com) is a good starting point.
One of the interesting online tools for troubleshooting ADFS is called Claims X-Ray. Claims X-Ray consists of a dedicated Relying Party Trust (RPT) in your ADFS environment. You can logon to the RPT automatically using the online tool, or manually via the ADFS IdpInitiatedSignon page (as discussed in my previous blogpost Implementing Active Directory Federation Services step-by-step)
The X-Ray Relying Party Trust can be created using the following PowerShell commands on your (primary) ADFS server:
[PS] C:\> {$authzRules = "=>issue(Type = `"http://schemas.microsoft.com/authorization/claims/permit`", Value = `"true`"); "
[PS] C:\> $issuanceRules = "@RuleName = `"Issue all claims`"`nx:[]=>issue(claim = x); "
[PS] C:\> $redirectUrl = "https://adfshelp.microsoft.com/ClaimsXray/TokenResponse"
[PS] C:\> $samlEndpoint = New-AdfsSamlEndpoint -Binding POST -Protocol SAMLAssertionConsumer -Uri $redirectUrl
[PS] C:\> Add-ADFSRelyingPartyTrust -Name "Claims X-ray" -Identifier "urn:microsoft:adfs:claimsxray" -IssuanceAuthorizationRules $authzRules -IssuanceTransformRules $issuanceRules -WSFedEndpoint $redirectUrl -SamlEndpoint $samlEndpoint
As shown in the following screenshot:

If you want to test the Claims X-Ray using oAuth you need to create the oAuth client using the following PowerShell commands, again on your (primary) ADFS server:
[PS] C:\> Add-AdfsClient -Name "Claims X-ray Client" -ClientId "claimsxrayclient" -RedirectUri https://adfshelp.microsoft.com/ClaimsXray/TokenResponse
[PS] C:\> if ([System.Environment]::OSVersion.Version.major -gt 6) { Grant-AdfsApplicationPermission -ServerRoleIdentifier urn:microsoft:adfs:claimsxray -AllowAllRegisteredClients -ScopeNames "openid","profile" }

When the Relying Party Trust is created you can continue with the online tool to test it, and thus have a closer look at your environment. In the Claims X-Ray tool enter the federation instance (i.e. federation.exchangelabs.nl) and click Test Authentication as shown in the following screenshot:

It will redirect to your WAP server (default ADFS behavior), enter valid user credentials and it will show the returned SAML token, including the claims it contains.
If I do this for my own environment, it will return a token with 21 claims which contain interesting information like the IP address of the originating client (userip or x-ms-forwarded-client-ip, where I ran the web browser), the IP address of the ADFS WAP server (x-ms-clientip), the type of browser I am using, whether I’m on the corporate network or not, the UPN, implicit UPN and Windows accountname to name a few. A couple of these claims are shown in the following screenshot:

It is also possible to use the IdpInitiatedSignon page, the Claims X-Ray RPT option is added to this page by the PowerShell commands:
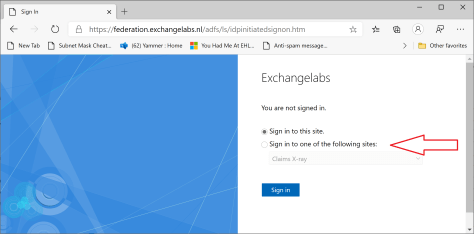
When you logon you’ll see a new token with different claims, depending on the location where you are logged on at that moment. While commuting in the train for example I can figure out the way I’m authenticated by ADFS and which claims are issued for this particular scenario:

Using the Claims X-Ray online tool you can test the behavior of your ADFS environment from different clients, networks etc. when you have to troubleshoot your environment, or if you are just interested.
For example, at the moment I’m working on an issue where we are difficulties with a MobileIron deployment that needs to authenticate against an ADFS deployment. The rules and policies from the regular RPT can be copied to the Claims X-Ray RPT, after which you can determine the behavior of the RPT, and hopefully figure out why it won’t work in the first place.
More information
Claims X-Ray – https://adfshelp.microsoft.com/ClaimsXray/TokenRequest
Thanks for the tip 😉 Eventually found and fixed the problem?
LikeLike
Don’t ask…. No, not yet
LikeLike