Every now and then we get a call from end users that they cannot login at Microsoft Teams and they get an error message “The request is not properly formatted” and “The parameter ‘login_hint’ is duplicated.“, especially after changing the user password. The error message is shown in the following screenshot:
This error message is recurring, so it’s not possible to logon anymore. It looks like there’s something stored in a cache related to the user’s old credentials. To resolve this, you can follow these steps:
- Exit the Teams client, and make sure Outlook is also closed since Outlook can have open add-ins related to teams.
- Go to the directory C:\Users\<username>\Appdata\Microsoft\Teams (shown below) and delete all files and directories found there. If any files cannot be deleted, most likely Outlook is still locking files.
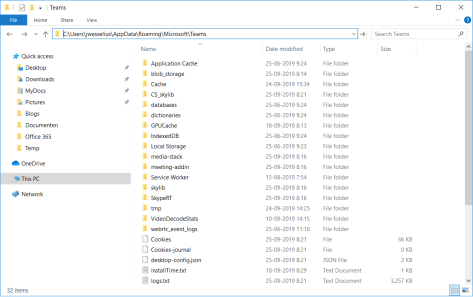
When all files are deleted you can start the Teams client again and it should logon successfully.
Now, I’ve seen a couple of times where the solution mentioned above is not working and the error keeps appearing. I’ve found the most strange, weirdest and (at this moment) unexplainable workaround 🙂
When the error occurs, close the Windows and the following We’re sorry – we’ve run into an issue window will appear:
Click signing out and try to sign-in again, but with a deliberate wrong domain, for example jaap@contoso.comm. Of course it will fail since it does not recognize the domain. Try again with the correct name (i.e. jaap@contoso.com) and it signs in successfully.
I think (but I’m not sure) the login caches some information somewhere, but I have no idea where. If you do, please let me know in the comments.






You must be logged in to post a comment.