In the previous two blog posts I’ve explained how to implement Exchange Online Protection as a message hygiene solution for your on-premises Exchange environment, both for inbound as well as outbound mail flow.
In this blog post I’ll go more into detail when configuring Exchange Online Protection
SPF, DKIM and DMARC
When Exchange Online Protection is fully up-and-running you can continue configuring SPF, DKIM and DMARC for message authentication purposes. This will make sure your email domain is much harder to spoof and receiving email systems know that the source of your email is a trusted source.
SPF
SPF has been around for years, and in my previous blog post I already mentioned the SPF record needed for use with Exchange Online Protection. If you want to read more about implementing SPF, please check my SenderID, SPF, DKIM and DMARC in Exchange 2016 – Part I blog post.
When only using Exchange Online Protection your SPF record will look like v=spf1 include:spf.protection.outlook.com -all.
DKIM
The good thing about Exchange Online Protection is that it supports DKIM signing and verification out of the box. The only thing you have to do is enable it in the Exchange Admin Center!
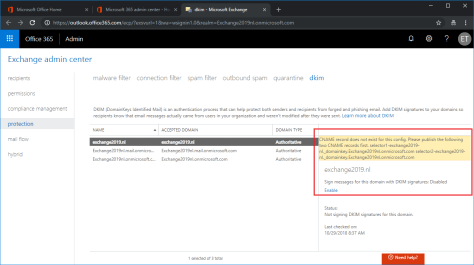
Logon to the Exchange (Online Protection) Admin Center, select protection in the navigation menu and click DKIM in the toolbar. When you click enable, an error message (in yellow) is shown that you need to create the appropriate DNS records first (click to enlarge).
The error message reads (for search engine purposes):
CNAME record does not exist for this config. Please publish the following two CNAME records first.
selector1-domain-com._domainkey.tenantname.onmicrosoft.com
selector2-domain-com._domainkey.tenantname.onmicrosoft.com
The description isn’t that clear when you’re not a DKIM guru, but you need to create the following CNAME records:
Selector1._domainkey.domain.com CNAME selector1-domain-com._domainkey.tenant.onmicrosoft.com
Selector2._domainkey.domain.com CNAME selector2-domain-com._domainkey.tenant.onmicrosoft.com
When the DNS records are created you can use the MXToolbox to check if they are valid: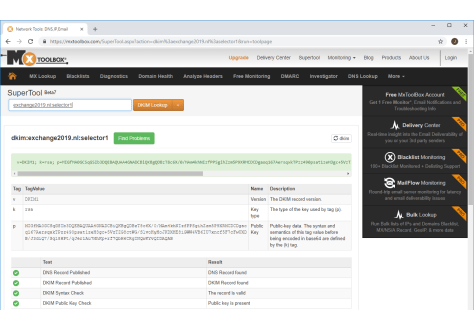
If an email is sent from the on-premises Exchange server via Exchange Online Protection to for example Gmail, you can check the headers. If configured correctly you can see the SPF check passes, you can see the DKIM signature created by EOP and you can see the authentication results as well. It should read spf=pass and dkim=pass under Authentication Results as shown in the following screenshot (click to enlarge):
For more information regarding DKIM and Exchange, please check my SenderID, SPF, DKIM and DMARC in Exchange 2016 – Part II blogpost.
DMARC
When DKIM and SPF are configured correctly you can create a DMARC record in public DNS. A DMARC policy will tell a receiving mail server what to do with email that does not comply with other settings. For example, if email is coming from a mail server that’s not listed in the SPF record it might well be spoofed. If the DKIM signature is missing it might be spoofed, if the DKIM signature is not valid, the message might be tempered with. If this is the case, you can define a policy that will reject such a message. The DNS record will be like this:
v=DMARC1;p=reject;sp=reject;pct=100;rua=mailto:dmarcreports@exchange2019.nl
The RUA is an email address where DMARC reports are sent to, so it’s a good thing to have such a mailbox on your Exchange server.
When sending an email from the Exchange server via EOP to Gmail when SPF, DKIM and DMARC are configured, you can see information like the following screenshot in the email headers (click to enlarge):
Everything is configured correctly now and spoofing is much harder to achieve for malicious users.
For more information regarding DMARC and Exchange, please check my SenderID, SPF, DKIM and DMARC in Exchange 2016 – Part III blog post.
Summary
In this blogpost I showed you how to configure SPF, DKIM and DMARC in Exchange Online Protection to prevent spoofing by malicious users.
In my next blog I’ll go more into detail about configuring the message hygiene options themselves in Exchange Online Protection.


I have EOP and on-prem 2016 exchange deployment. The option to enable DKIM in EOP doesn’t exist and simply states: “No DKIM keys saved for this domain”. I also don’t see DKIM in the exchange management console. Do you have any thoughts or links to how to configure DKIM in this scenario?
LikeLike
Hi Matt, this is strange, never seen this before. What happens if you use a Get-DkimSigningConfig? Do you get any results?
You can try to create a new one using New-DkimSigningConfig -DomainName yourdomain.com -Enabled:$true
LikeLike