If you have a smaller organization and you want to assign Office 365 licenses that’s no big deal. Open the user properties in the Microsoft Online Portal and assign the proper license. If needed you can assign only specific services without too much hassle. Besides using the Portal it is also possible to use PowerShell to assign licenses as discussed in an old blog: https://jaapwesselius.com/2014/09/04/assign-office-365-license-via-powershell/
For larger organizations this can be cumbersome and prone to error. Also, when using a dedicated provisioning solution it can be tricky. An interesting solution is to use Group based licensing. You can assign Office 365 licenses to a security group and when a user is added to this group, the user automatically gets the assigned licenses.
In this example we’re going to implement Group based licensing. First we are going to create a baseline where only the basic features of Office 365 E3 are implemented. Next we are going to create another option where additional features are added.
- Labs_O365_E3_Base
- Labs_O365_E3_TeamsAndPlanner
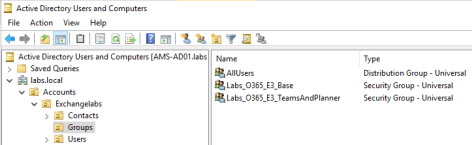
After synchronization these groups will show up in Azure Active Directory:
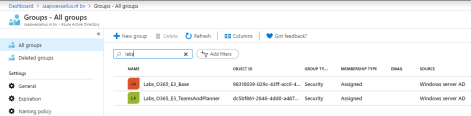
The next step is to assign the licenses to these security groups.
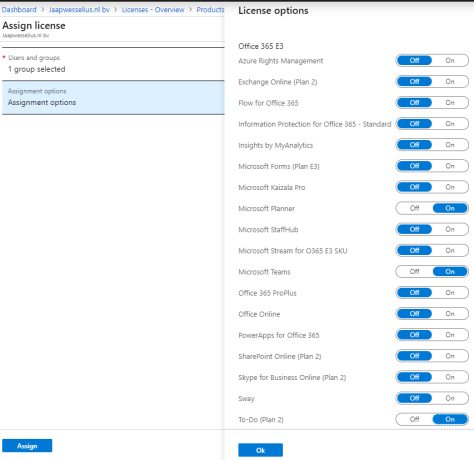
In the Azure Portal, select Azure Active Directory | Licenses | Office 365 E3 and click + Assign. In the Users and Groups box select the first group (Labs_O365_E3_Base in this example) and in the Assignment Options box select the options you want to assign to this group:

Use the same steps to assign additional options to the second group:
When you create a new user in Active Directory and add this user to the base security group, you’ll see that the user will receive only the licenses assigned to the group. If you want to assign more license options, just add the user to the additional group. This way you are very flexible in assigning licenses, and chances on errors are minimized.
Note. You can assign licenses directly on the user object or using security groups, it is not possible to combine both. So, if you use groups to assign licenses it is not possible to add additional licenses directly on the users object in the Office 365 Portal.
More information
- Assign licenses to users by group membership in Azure Active Directory – https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/licensing-groups-assign






You must be logged in to post a comment.