On February 10, 2025, Microsoft released Cumulative Update 15 for Exchange 2019, also called the 2025H1 Update, the first step towards Exchange Server SE. CU15 is an interesting and essential update since it is the last major update for Exchange 2019. The next major update that Microsoft will release is Exchange Server Subscription Edition (SE) later this year.
Exchange 2019 CU15 comes with several new features:
- Support for Windows Server 2025, but it can also be installed on Windows Server 2022 and Windows Server 2019. Windows Server 2025 has a slightly different set of prerequisites server roles and features, mainly because of the absence of the SMTP stack in Windows Server 2025.
When you want to install Exchange CU15 on Windows 2025 please be aware that you cannot in-place upgrade the underlying Operating System, so you need to install a new server (and a new DAG if you are currently using one).
As a side note, running Exchange 2019 CU14 on Windows Server 2025 is now also supported, including Domain Controllers on Windows Server 2025. - Support for TLS 1.3. Exchange 2019 CU15 supports TLS 1.3, but unfortunately, it is only supported by HTTPS for client use. TLS 1.3 for SMTP is not supported yet, but it is expected to be released in a future update.
- Feature Flighting. This is also used in Microsoft 365 and allows for the gradual release of new features using so-called ‘rings’.
- Certificate Management is available again in the Exchange Admin Console.
- AMSI body scanning for anti-malware. Remote Code Execution malware is always post-auth, and it can be prevented using AMSI body scanning.
- ECC Certificates (Elliptic Curve Cryptography) are now supported on the Edge Transport Server and for POP3 and IMAP4.
- And important update: Exchange 2013 coexistence is not supported with Exchange 2019 CU15! This is hardcoded in the setup application! If you are still running Exchange 2013 and planning to move to Exchange 2019 you have to move to CU14 first and decommission Exchange 2013 before moving to CU15.
- CU15 also includes all security updates that were released in the November 2024 Security Update and it includes the fix for the timezone issue.
- And, of course, a lot of other issues are resolved in Exchange 2019 CU15.
Windows Server 2025
Exchange 2019 CU14 and CU15 are now supported on Windows Server 2025. Windows Server 2025 has some changes compared to earlier Windows versions, for example the SMTP stack and the legacy Web Management Console are no longer available.
As a result, the prerequisites have changed a little, unfortunately, the VC++ updates and the UC Managed API must still be installed, and the MSMQ must still be installed. The complete list of prerequisites can be found on Exchange Server Prerequisites.
Active Directory & Schema changes
There are no Active Directory Schema changes, so this remains at version 17003.
There are changes to the Configuration container, which is now at version 16763. To update the Configuration container, execute the following command from the Exchange 2019 CU15 installation media:
Setup.exe /PrepareOrganization /IAcceptExchangeServerLicenseTerms_DiagnosticDataOnIf you don’t want to send diagnostic data to Microsoft, you must replace the ‘On’ in the previous command with ‘Off’.
There are also no changes in the Domain partition, this version remains at 13243.
All information about Schema Changes can be found on Active Directory schema changes in Exchange Server.
TLS 1.3
TLS 1.3 is supported and enabled on Windows 2022 and Windows 2025. If you are still running Exchange 2019 on Windows 2019, you must install a newer version of Windows Server first.
Exchange 2019 CU15 will enable TLS 1.3 for new installations and for in-place upgrades. If you do not want this you can block this using the following registry, prior to installing Exchange 2019 CU15:
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\ExchangeServer\V15\Setup" -Name "SkipTLS13ActivationDuringSetup" -Value 1 -Type StringAssuming you already have Exchange 2019 running and therefore have TLS 1.2 make sure all your servers, clients, applications, load balancers and device support TLS 1.3.
Enabling TLS 1.3 on your server consists of several steps:
- Preparing .NET Framework to inherit defaults from Schannel
- Enabling Strong Cryptography
To do this, run the following PowerShell commands:
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" -Name "SchUseStrongCrypto" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319" -Name "SchUseStrongCrypto" -Value 1 -Type DWordMicrosoft recommends to set the same registry keys for .NET Framework 3.5. Although this is not used in Exchange 2013 or later, it is recommended for an identical configuration. To do this for .NET Framework 3.5 inheritance, execute the following PowerShell commands:
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" -Name "SchUseStrongCrypto" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727" -Name "SchUseStrongCrypto" -Value 1 -Type DWordTo enable TLS 1.3 for both Server and Client connections, execute the following PowerShell commands:
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols" -Name "TLS 1.3" -ErrorAction SilentlyContinue
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3" -Name "Client" -ErrorAction SilentlyContinue
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3" -Name "Server" -ErrorAction SilentlyContinue
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client" -Name "DisabledByDefault" -Value 0 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client" -Name "Enabled" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server" -Name "DisabledByDefault" -Value 0 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server" -Name "Enabled" -Value 1 -Type DWordFinally, to configure the cipher suites for TLS 1.3, execute the following PowerShell commands:
Enable-TlsCipherSuite -Name TLS_AES_256_GCM_SHA384 -Position 0
Enable-TlsCipherSuite -Name TLS_AES_128_GCM_SHA256 -Position 1So, how do you know this works? The easiest way to find out is to use OWA and after logging on to a mailbox, start developer mode (using the F12 button) in your browser. Select ‘Security’ (when not available, click the + icon to select the security button) and check the connection as shown in the following screenshot:
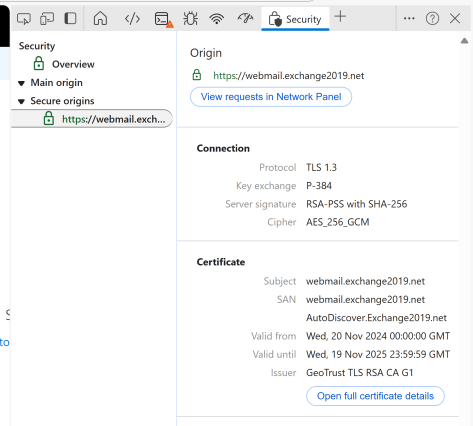
As stated in the beginning of this blog, right now TLS 1.3 is only supported for HTTPS connections. Support for TLS 1.3 for SMTP will be available in a future update for CU15.
Feature Flighting
Feature Flighting is a new cloud-based solution for gradually deploying new features in Exchange Server . On the Exchange server, Feature Flighting uses a new service (MSExchangeFlighting) that checks the Office Config Service (OCS, the same endpoint that’s used for EEMS) every hour for new Feature Flight Definitions (FFD). Based on so-called ‘rings’, new features are deployed and activated. Feature Flighting is introduced in CU15, but there are no plans to release any features that can be ‘flighted’ into CU15. This will be available in Exchange Server SE.
Deployment and activation is based on ‘rings’ which define the action that must be taken when new features become available. The following rings are available:
| Ring | Name | |
| 0 | Early Adopter | This is the earliest ring and used for testing new updates. Updates are immediately activated after an update is installed. |
| 1 (default) | Worldwide Ring | Default ring when an Exchange 2019 CU15 server is installed. Updates are received when Microsoft confirmed features are available for general availability. |
| 2 | Admin Action | New updates are not automatically enabled and it allows admins to roll-back newly enabled features. Features are shipped in a disabled state in this ring. |
To view the ring level of your Exchange servers, execute the following command in Exchange Management Shell:
Get-ExchangeServer | select Name,RingLevelAnd to change the ring level, execute a PowerShell command similar to this:
Set-ExchangeServer -Identity EXCH01 -RingLevel 2To request features and their state, you can use the following PowerShell command:
Get-ExchangeServer -Identity CU15-1 | Select Name,RingLevel,Feature*
Name : CU15-1
RingLevel : 1
FeaturesApproved : {}
FeaturesAwaitingAdminApproval : {}
FeaturesEnabled : {PING.1.0}
FeaturesBlocked : {}
FeaturesDisabled : {}More information regarding features can be retrieved using the Get-ExchangeFeature command:
Get-ExchangeFeature -Identity EXCH01
Server FeatureID RingLevel Status Description
------ --------- --------- ------ -----------
EXCH01 PING.1.0 1 Enabled HeartBeat Probe. Validates the Telemetry ChannelWhen new features become available, they are listed in the FeaturesAwaitingAdminApproval property. To approve a new feature with a new like Feature.1.0, use a PowerShell command similar to the following:
Set-ExchangeFeature -Identity EXCH01 -FeatureID "Feature.1.0" -ApproveLikewise, to block this new feature, a command similar to the following can be used:
Set-ExchangeFeature -Identity EXCH01 -FeatureID "Feature.1.0" -ApproveNote. Feature Flighting is only available for Mailbox servers, not for Edge Transport servers or Management servers. The Mailbox server needs an internet connection since Feature Flighting updates are released online.
Exchange 2013
This is an important note if you are still running Exchange 2013. As of April 11, 2023, this version of Exchange is no longer supported. It is considered persistently vulnerable and, therefore, not supported in coexistence with Exchange 2019 CU15. This is hardcoded in the setup application! If you are still running Exchange 2013, you must first upgrade to Exchange 2019 CU14 and fully decommission Exchange 2013 before you can upgrade to Exchange 2019 CU15.
More information can found in Microsoft knowledgebase article KB5042461 and the download can be found at https://www.microsoft.com/en-us/download/details.aspx?id=106402.
As always, test all aspects of CU15 in a safe test environment to determine how it will impact your own environment. Better safe than sorry!




You must be logged in to post a comment.