One option, not only for security, but also for user convenience is Self Service Password Reset (SSPR). This feature enables cloud users to reset their own passwords in Azure Active Directory, and this way they don’t have to contact the local IT staff with reset password questions.
Note. For Self Service Password Reset you need an additional Azure AD Basic license.
To enable Self Service Password Reset, logon to the Azure Portal (https://portal.azure.com) as a Global Administrator. Select Azure Active Directory, select Password Reset and in the actions pane, select Selected or All. Using the Selected option, you can enable SSPR only to member of the security group SSPRSecurityGroupUsers for a more targeted approach. Of course, if you want to enable SSPR for all your users you should select the All option.

Click Save to store your selection. Click the second option Authentication Methods to select the number of methods available to your users. In my example, I’m going to select just one, and options I select are Email and Mobile Phone.

Click Save to continue. The last step is to configure the registration. This is to require users to register when signing in, and the number of days the users are asked to re-confirm their authentication information, as shown in the following screenshot:
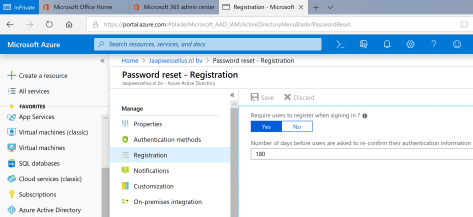
You’re all set now.
When a (new) user logs on now, he is presented with a pop-up, asking for verification methods. As configured earlier the authentication phone and authentication email is used. The mobile phone number that’s presented here was configured earlier in Azure Active Directory when provisioning the user. Click Verify and you’ll receive a text message with a verification code.
You can chose an email address for authentication purposes, as long as it’s not an email address in your own tenant. Follow the wizard when you click Set it up now as shown in the following screenshot.

To test the SSPR, use the browser van navigate to https://passwordreset.microsoftonline.com/, enter your userID (UPN) and enter the CAPTCHA code.
You can choose to send an email to your verification account, send a text message to your mobile phone (see screenshot below) or have Microsoft call you.

Enter your phone number (the phone number that’s also registered in Azure AD) and within seconds you’ll receive a verification text message. After entering this code you can enter a new password, and with this new password you can login again.
As a bonus you’ll receive an email that you password has been changed.
Summary
In this blogpost I’ve shown you how to implement the Self Service Password Reset (SSRP), a feature that’s available in the default Office 365 Enterprise licenses, so no additional Azure AD licenses are needed. You can choose to implement text messages or email messages (as shown in this blogpost) but you can also implement additional security questions.
Now this is a nice solution for cloud identities, but it does not work for synced identities or federated identities. For this to work you need to implement password write-back, a nice topic for the next blog 😊


















You must be logged in to post a comment.